KringleCon | Yule Log Analysis | CTF Challenge Solution
Pepper Minstix: Yule Log Analysis
As part of this challenge, we are looking at Microsoft Event Viewer Logs to discover an instance of password spraying that eventually succeeded. Password spraying is when attackers use different usernames in rotation to attempt login. This is done to prevent account lockout during password guessing or brute forcing. For example, if an attacker provides incorrect password more than 3 times within a certain time period for the same account, they would be locked out. However, if they tried the same password for different usernames, they would buy themselves more time before hitting the same username again with a different password. This has the potential to prevent account lockout which allows the attackers to keep going.
We are to look for evidence of password spraying in the logs and zero in on an instance when the attackers were able to successfully login as a user. The solution to the challenge will then be the user that the attackers logged in as. We are provided with a python log parser that is able to read the logs and provide us with intelligible logs. As expected, there is a lot of events in the logs which would take us a long time to manually go through. So we need to write regex or grep queries to quickly locate events of interest. Let’s take a look at the logs:
evtx\_dump.py ho-ho-no.evtx | more
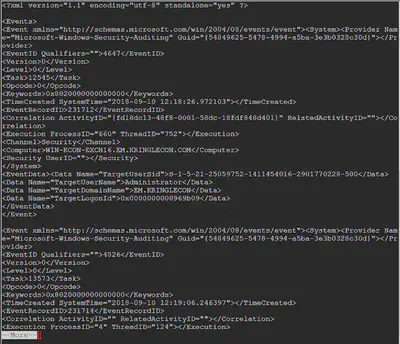
It’s a markup format with each event enclosed with the <Event> tags and identified with EventID. To understand the EventIDs, we refer to this resource online. Basically, we need to understand what these event IDs imply. Looking at the resource, we are able to determine that EventID 4624 refers to a successful login where as 4625 means that an account failed to logon.
ID
Message
4624
An account was successfully logged on.
4625
An account failed to log on.
A password spraying attack would involve a series of 4625 events with different usernames. In this case, we are investigating a successful login by the adversary so we know that it will be a series of 4625 event, followed by a 4624 event (successful login). Then to solve this challenge, we have to extract the username from that 4624 event. So let us begin analyzing the logs with this information in mind.
First, let’s look for a lot of 4625 events to identify our adversary:
evtx\_dump.py ho-ho-no.evtx | grep "4625" -A 20 -B 20
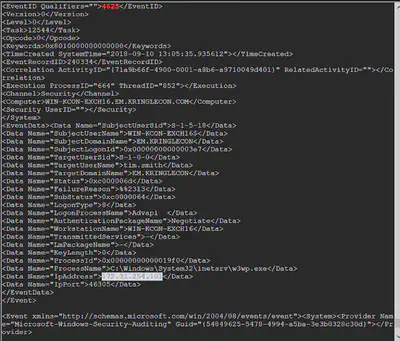
Looks like a majority of the 4625 events are initiated by the remote IP address: 172.31.254.101. So I’m thinking that is our threat actor. Note that their SID is S-1-5-18. Now using this information, we zero in on their activities – particularly, we try to figure out where they got a 4624 event (meaning they successfully logged in).
evtx\_dump.py ho-ho-no.evtx | grep 'ess">172.31' -A 10 -B 35 | grep "S-1-5-18" -A 22 -B 16 | grep "4624" -A 35 -B 1
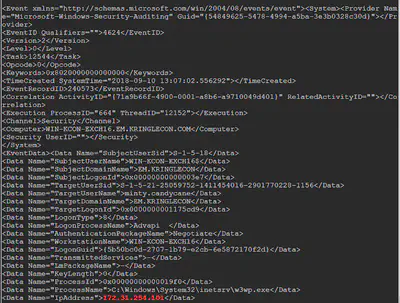
This record clearly shows that the threat actor 172.31.254.101 logged in successfully (4624) with the username minty.candycane.
Answer: minty.candycane