Local PHP File Inclusion Vulnerability Example | Web Applications Hacking | How To | LFI PHP
The vulnerability lies in how web pages are invoked on a web server. If an absolute path or direct referencing is used then it is possible to invoke pages on the server that a hacker has no business seeing.
You can read up on the theory here.
How To Exploit Local PHP File Inclusion Vulnerability on a Web Server | Mutillidae
Attacked Server: 1. Mutillidae 2. Net-force
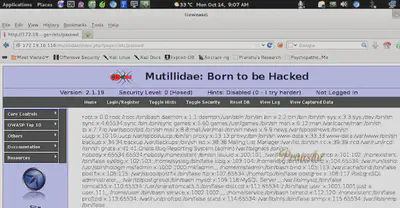
Vulnerable Page: /mutillidae/index.php?page=
Attack Type: Local PHP File Inclusion
A hacker notices that a GET Parameter ‘page’ is used to ‘include’ pages residing on a web server.
We know the web server is running on a Linux system. So we try to invoke the password file in Linux by specifying it’s absolute path:
page=/etc/passwd
If the web server was running on Windows system we could test the same trying to invoke:
page=C:\\boot.ini
The contents of the file would be displayed on the screen if Local File Inclusion exists:

Notice the Password Hash for the user NetForce. This can be cracked by johntheripper [JTR].
Such attacks can be avoided by not using absolute paths while referencing web pages on servers or using if-else structures to call specific pages only or encoding the attackers request (/etc/passwd).