KringleCon | Tangle Coalbox & de Bruijn Sequences | CTF Solution
Tangle Coalbox: Lethal ForensicELFication
The poem that introduces the challenge talks about certain “text editors” leaving behind clues. Vim immediately comes to mind. We know that Vim logs information about deletions and searchers into a file called .viminfo.
By default it is stored at ~/.viminfo. The dot (.) represents a hidden file. So we perform a file listing with -a option to see the hidden files. We notice .viminfo and pull out its contents. We notice that a search and replace was done that substituted the word Elinore with NEVERMORE.
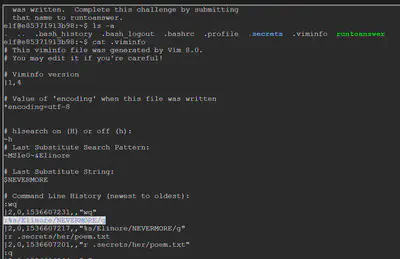
We can turn off Vim logging by using :set viminfo=
Answer: Elinore
Question 3 de Bruijn Sequences
This question asks us what welcome message greets the speaker. If we look at the website that holds the door authentication challenge, we find that the welcome message is exposed in the HTML.
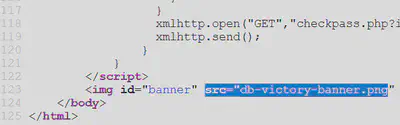
This allows us to directly access the victory banner image and gather the victory message and complete the challenge. However, to actually unlock the door, we can either follow the suggested de Bruijn Sequences or perform an exhaustive search for the permutation that opens the door. There are only 4 x 4 x 4 x 4 = 256 possible candidates. I decided to brute force it and used Burp Suite Intruder to send all possible candidates to the server and notice which one garners a positive response from the server.
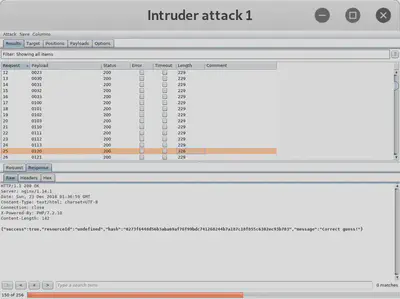
We notice that the sequence 0120 was accepted as the correct guess by the server. So we now know that the correct sequence of shapes is as follows:

Answer: Welcome unprepared speaker!