KringleCon | Stall Mucking Report & Data Repo Analysis | CTF Challenge Solution
Wunorse Openslae: Stall Mucking Report
We are told that a Samba share with shared network credentials is used to upload the file on the server. These shared credentials can be revealed via ps if they were entered in command-line mode. We use ps with the -e (view every process on system) and -ww (unlimited width) flag to reveal the username and password used for uploading the report.
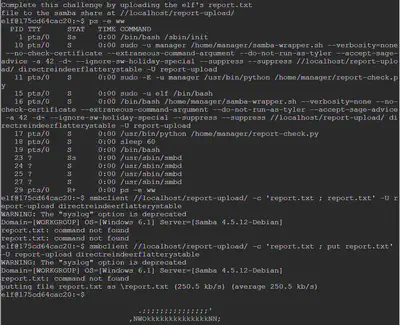
Once we have the credentials, we can use them to upload the report using smbclient:
smbclient //localhost/report-upload/ -c ‘report.txt ; put report.txt’ -U report-upload directreindeerflatterystable
Bonus
The password to the Samba share (directreindeerflatterystable) seems to be a play on correcthorsebatterystaple – the xkcd comic.
Suggested remediation: Using something like secret-tool to look up passwords in the Gnome keyring is safer than passing credentials in the command-line or storing them in a file.
Question 4
Wunorse Openslae gave us the tip to use the tool ‘truffleHog’ to dig through code repositories for exposed credentials. TruffleHog searches through repos, locating strings with high entropy. Sensitive information such as passwords traditionally have higher entropy. This tool was a great find for me and it quite straightforward to use. It was able to locate the password in the North Pole Git repository in no time.
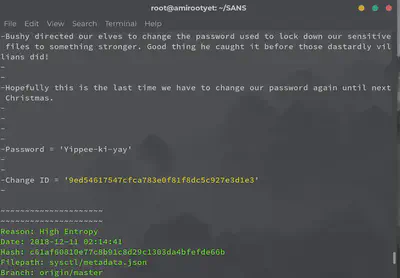
trufflehog https://git.kringlecastle.com/Upatree/santas\_castle\_automation
So much for “hopefully this is the last time we have to change our password against until next Christmas”.