KringleCon | The Name Game & Directory Browsing | CTF Challenge Solution
Minty Candycane: The Name Game
This challenge presents us with an onboarding system written in Powershell. There’s a command injection
vulnerability in the system that allows us to injection arbitrary commands after the ; is used to end the previous
query. For example, we can select option 2 in the onboarding system, and inject:
; sqlite3 ;
This allows us to enter the sqlite environment where we can query the database to discover the relevant
information as shown in the figure.
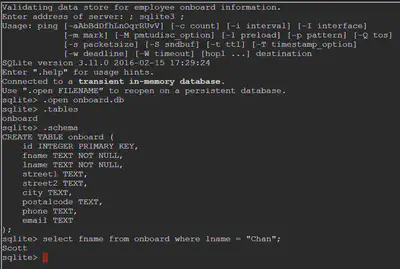
Answer: Scott
Question 2 Directory Browsing
This one a simple directory traversal vulnerability where when we click on ‘apply now’, we are redirected to the
following URL:
https://cfp.kringlecastle.com/cfp/cfp.html
If we remove the cfp.html and try to navigate to the cfp directory, the directory traversal vulnerability is apparent.
The files in this directory are listed for everyone on the Internet to see. We can now access ‘rejected_talks.csv’
which gives us the information we need to progress to the next challenge.
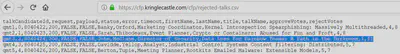
Answer: John McClane