KringleCon | Dev Ops Fail | CTF Challenge Solution
Sparkle Redberry: Dev Ops Fail
In this challenge, we are asked to see if there are any credentials exposed as a result of git operations. We list the contents of the current directory and notice the directory containing the git repository. Once we cd into this directory, we see the files within the repository.
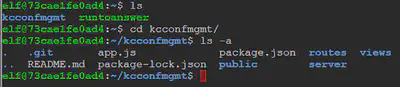
Judging by what the challenge has provided us so far, at some point, one of these files contained sensitive credentials hardcoded into it and then the repository was updated to remove them. To verify this, let us take a look at the git commit history:
git log
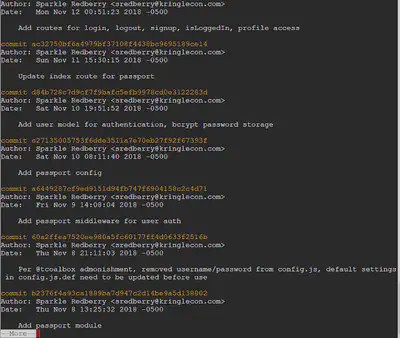
Notice git commit 60a2ffea7520ee980a5fc60177ff4d0633f2516b is when the username/password was removed from config.js. So we want to revert the repository back to the state right before that commit. The commit right before that was ‘b2376f4a93ca1889ba7d947c2d14be9a5d138802’, so let us revert back to it.
git reset --soft b2376f4a93ca1889ba7d947c2d14be9a5d138802
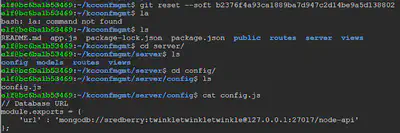
We can now see the credentials hardcoded in the config.js file.
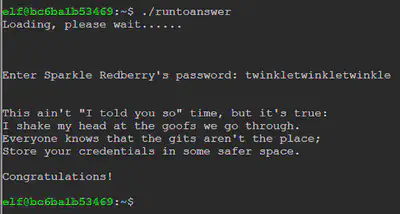
Password: twinkletwinkletwinkle