Hacking With Armitage on Kali Linux / Backtrack
If you are beginning to learn, Armitage is not something you would want to start with. It is alright to quickly automate some routine Metasploit tasks using Armitage, but if you’re trying to learn something, Armitage adds a level of abstraction and makes you a perfect script kiddie.
Learning stuff on msfconsole or msfcli before moving on to Armitage, is a better approach in my opinion.
The tool is mostly self-explanatory due to its GUI.
Here, I am simulating an attack on a Windows XP system using Armitage on Kali Linux.
Bring up Armitage by typing:
service postgresql start
armitage
First, I need to ‘discover’ this host.
Hosts -> nmap scan
OR, I could manually ‘add host’ by providing its IP.
Now I can see this windows XP host in Armitage workspace. From here, I could manually search for vulnerabilities on the Windows XP and then try to exploit them, but I chose the easy way on Armitage, which is ‘Hail Mary’.
Attacks -> Hail Mary
It tried some common exploits relating to available services on victim machine and gave me the ‘red’ around that host, which means the host is compromised.
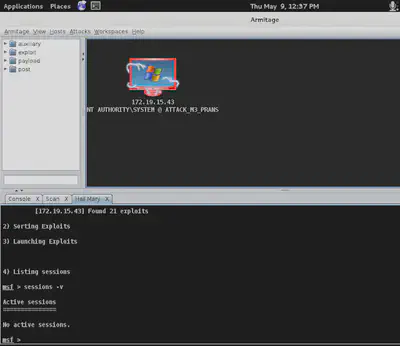
I grab the password hashes that I can try to crack later on.
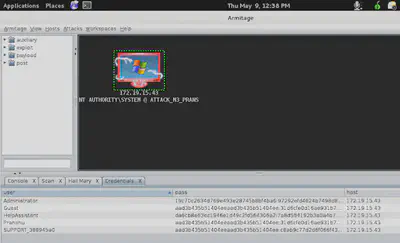
I gain access to cmd.exe ‘command prompt’ in windows.
I set up a persistant Meterpreter backdoor on the hacked windows XP for later access.
I view the processes running on hacked machine.
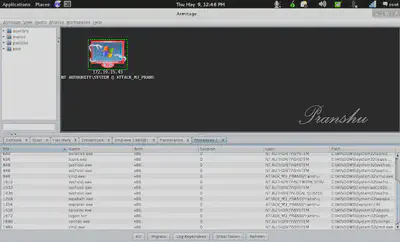
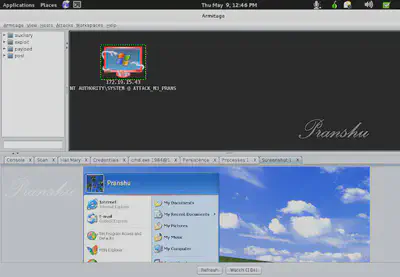
I take screenshots of activities on the hacked machine.
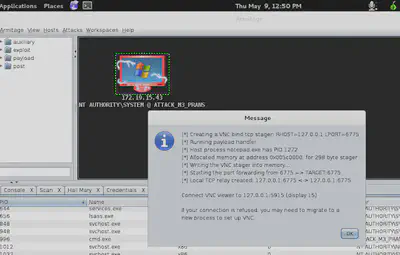
I tried connecting with VNC viewer to the remote machine.

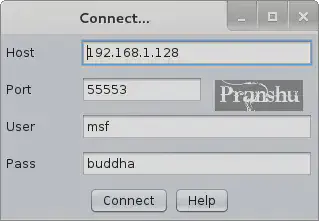
If you’re a part of a pentest team, then one of you can host an Armitage server and other can ‘connect’ to it, so that you can collaborate on the project.
In the connect window, you need to enter the host name of the fellow pentester hosting the Armitage server, the port number, and the username and password that he/she has provided you.
At the next window, confirm the fingerprint.
Pick a ‘Handle’ for the session.
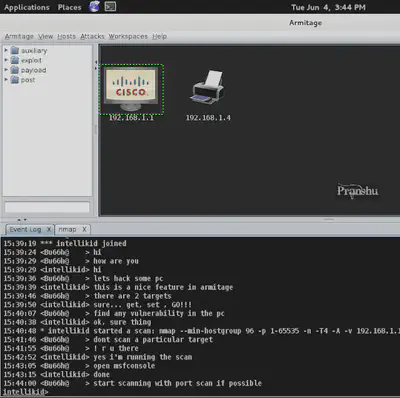
And then you can join in with your Pen Test Team and work in collaboration on the project
There’s a bunch of other stuff you could do with Armitage, please feel free to explore further.