Basic XSS Attacks Demo and Examples
Cross site scripting attacks are common. But for people new to penetration testing, they may seem a little convoluted at first (specially in case of beginners who don’t have much experience with web languages). There’s a whole lot of theory available all over the web on XSS so I’m not getting into that.
Given below are some of the simplest demonstrations of cross site scripting attacks.
This is a simple webpage:
http://www.insecurelabs.org/task/Rule1
As a penetration tester, you would study the page and try to inject code in their search box:
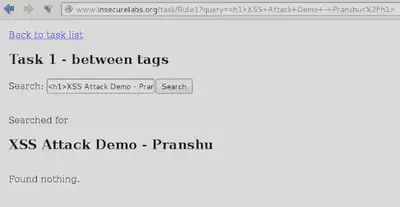
<h1>XSS Attack Demo - Pranshu</h1>
Press enter and notice the dialogue box on the screen. Also, notice the use of header tags of HTML.
Nowm let’s try the following in the search box:
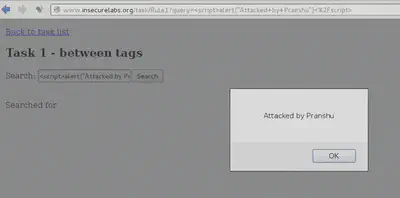
<script>alert("Attacked by Pranshu")</script>
See the window alert?
You can even try a new window pop-up that can be used to open a new website (although most browsers now have pop-ups blocked by default)
Link sent to Victim would look like

You can also try other stuff like displaying an “evil” image on the website (kind of like defacing it but not really)
<html><body><img src="http://fc05.deviantart.net/fs71/i/2012/257/8/b/hacker\_skull\_wallpaper\_by\_simon93\_ita-d5enmvk.jpg"> </body> </html>
Link sent to victim:
http://www.insecurelabs.org/task/Rule1?query=%3Chtml%3E%3Cbody%3E%3Cimg+src%3D%22http%3A%2F%2Ffc05.deviantart.net%2Ffs71%2Fi%2F2012%2F257%2F8%2Fb%2Fhacker\_skull\_wallpaper\_by\_simon93\_ita-d5enmvk.jpg%22%3E+%3C%2Fbody%3E+%3C%2Fhtml%3E
In this case, the victim would follow your link and see something like this:
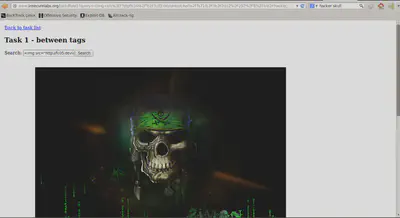
Remember: The website is not actually defaced. It is just an “illusion” for that particular user who followed your specially crafted link.
In reality, why would the victim put this stuff in Search box? They won’t. So we send them this malicious link which is specially crafted by the attacker:
http://www.insecurelabs.org/task/Rule1?query=%3Cscript%3Ealert%28%22You+are+Attacked+by+Pranshu%22%29%3C/script%3E
A hacker will post something like this on a forum (somewhere where a lot of people can see it):
Hey guys!! New stuff on insecurelabs, check it out. Here’s the link:
Now to a savvy user the included script tags would be a dead giveaway, but to a normal user, its just a link on insecurelabs.org and they might click it.
Now imagine if in place of the harmless alert box, we point them to a malicious JavaScript code that get executed on their browser. Such a code can be used to steal cookies stored on the victim’s machine.
Note: It is important to realize that though the victim ends up being exploited, the vulnerability actually lies on the web server. This is why many bounty hunters these days go after bounties that are awarded for discovering such flaws on a website that might affect its users.